As effective as it is, the Tor network has never really gone mainstream as an avenue for enhanced privacy and anonymity. Much of that is down to performance issues and a reputation for being riddled with bad actors. On the other hand, Virtual Private Networks have steadily gained traction as people become more concerned with privacy in an evolving world. They serve somewhat similar purposes. So, Onion over VPN combines both technologies to provide maximum protection for its users.
It’s the best of both worlds. Or is it? This article will show you all you need to know about Onion over VPN. But first, an overview of both services.
What is a VPN?
A Virtual Private Network is a tool that establishes a secure and encrypted connection over a public network, like the Internet. VPNs allow users to create a private network connection that shields their online activities from prying eyes.
Here’s how it works. When you use a Virtual Private Network, your internet traffic moves through a remote server operated by the provider. This server is an intermediary between your device and the websites or online services you visit.
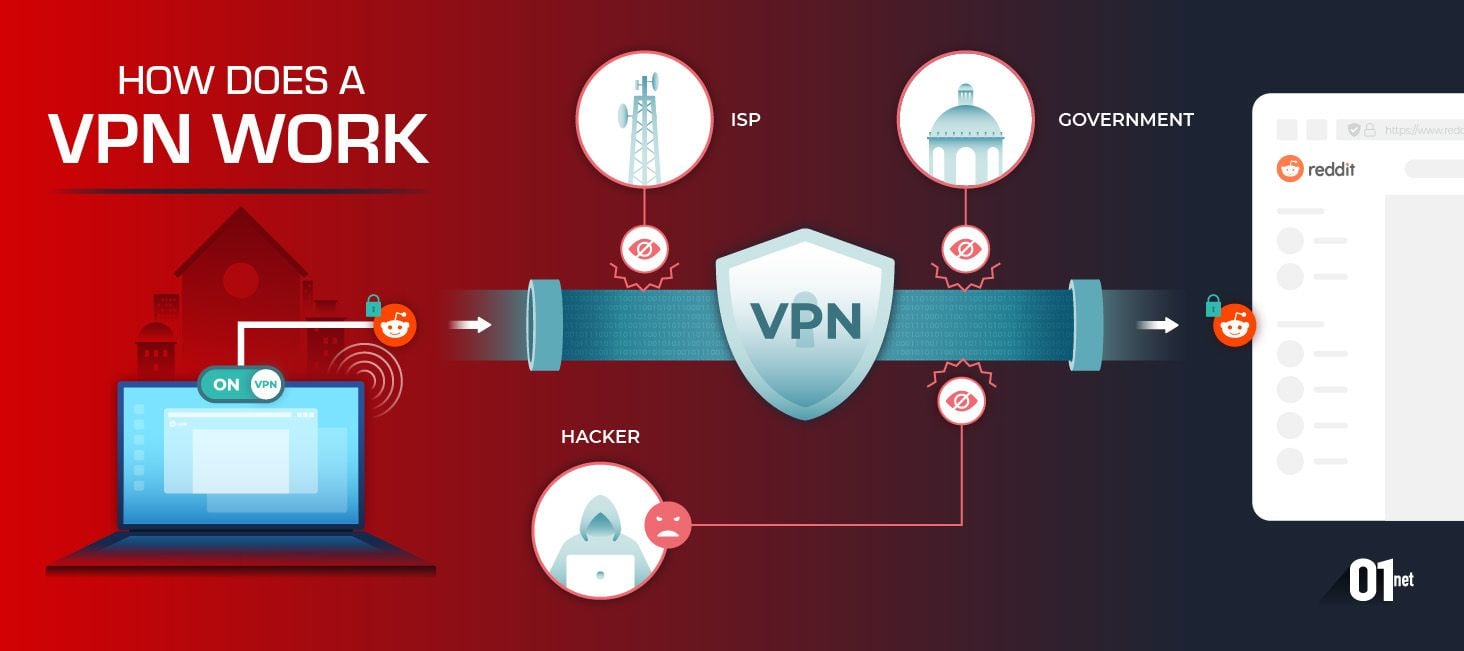
The data transmitted between your device and the VPN server is encrypted, making it difficult for third parties to decipher. And if you’re wondering just how secure that is, it would take the right quantum computer 2.29 x 10^32 years to crack AES-256, the encryption used by the top VPNs.
That’s an incredibly long time.
VPNs mask your IP address and make it appear like you’re accessing the internet from a different location. That way, your identity and location stay private from potential tracking and surveillance.
They also come in handy for things like bypassing geo-restrictions on streaming services and providing remote access to private networks.
What is the Tor Network?
Tor (short for The Onion Router) is an open-source network designed to provide anonymity when accessing the Internet.

Think of an onion and its layers. Onion routing is built on that principle, using multiple layers of encryption to protect its users’ identities and online activities.
When you use Tor, your internet traffic gets bounced around three volunteer-run nodes, encrypting and decrypting the data at each step. Because they are randomly assigned nodes, tracing the data back to the original source is incredibly difficult.
The Tor network is the closest thing to complete anonymity. That’s why it’s so attractive to journalists, activists, or whistleblowers nervous about surveillance.
But it also attracts more malicious users. Tor has gained a shady reputation due to its association with certain activities, such as drug trafficking, hacking, and other forms of cybercrime. And not all node volunteers share the same motives.
What’s more, due to your traffic’s routing through various nodes, your connection speed reduces significantly.
How Does Onion Over VPN Work?
Virtual Private Networks and Tor are similar technologies, but they are not interchangeable. Pairing them reinforces their individual weaknesses. In essence, Onion over VPN leverages the strengths of both systems to provide amplified levels of privacy and protection.
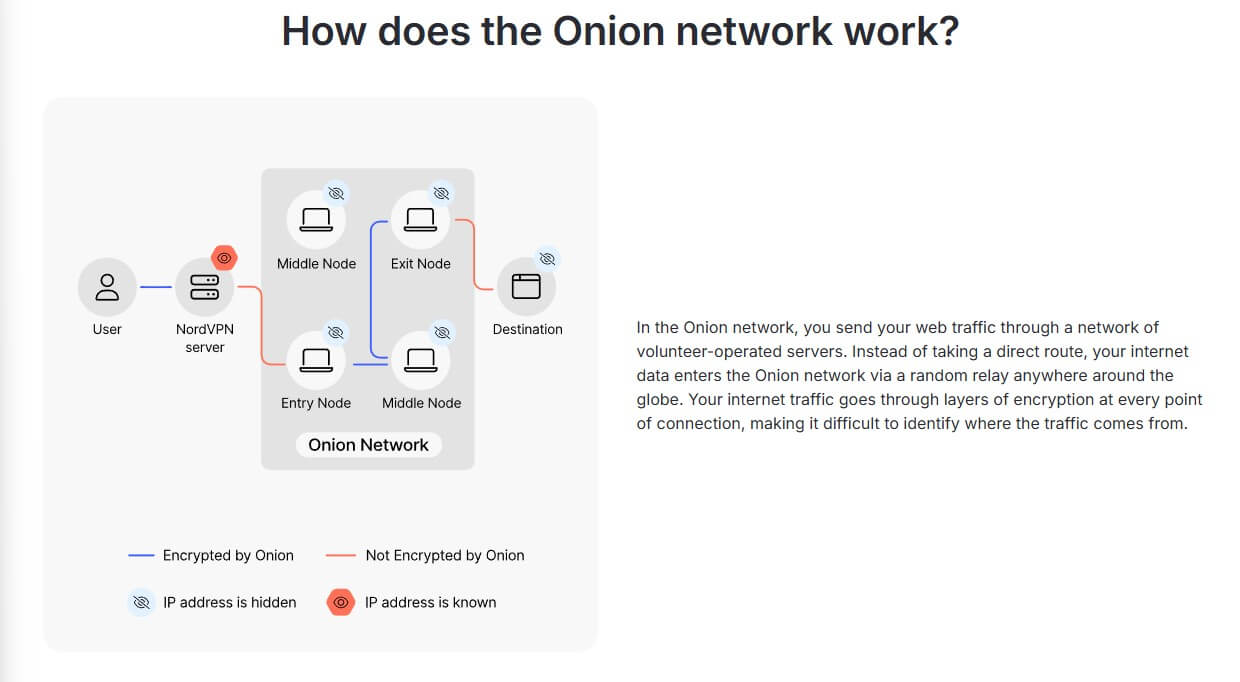
It works like this. You connect to a VPN server, and your Internet traffic gets encrypted and routed through the tunnel, ensuring your data remains confidential. This initial step shields your IP address and secures your online activities.
But it goes further than that. After the encryption within the tunnel, your traffic is passed through the Tor network when you use the Tor browser.
It enters through an entry node, which strips the initial VPN layer of encryption. From there, the data passes through a series of random nodes within the network, getting encrypted and decrypted before arriving at its destination.
What happens when you receive information from a website? First, Tor encrypts that traffic, which is relayed through the network. Then the VPN encrypts it again before sending it over to your device. From there, Tor decrypts it and your VPN repeats the process.
The Benefits of Onion Over VPN
Let’s discuss the advantages of using the VPN-Tor hybrid.
- It provides an extra layer of encryption. There are several encryption points as your data flows from your device to the Internet and back. Consequently, any entity trying to decode is bound to have a hard time.
- You can use the Tor network where it’s blocked, such as at your office or school. Onion over VPN disguises your connection and makes it appear as regular traffic.
- Volunteers operate onion servers, so bad actors can deploy compromised servers. However, Onion over VPN hides your IP address from the entry node, protecting you against potential monitoring within the Tor network.
- Because of the negative connotations attached to it, you may prefer to keep your Tor use private. Without a Virtual Private Network, your ISP can see when you use Tor. This system prevents that from happening.
The Drawbacks
While it has several benefits, maybe you should reconsider using Onion over VPN, considering these points:
- There’s a performance trade-off. Both a VPN and Tor negatively impact your connection speeds (though a VPN does so significantly less). You should expect even slower speeds when used together, as your traffic has to pass through more points.
- Some sites block Tor exit nodes. Since that’s the final point before your traffic reaches the internet, you’ll be unable to access those websites.
- The exit note is vulnerable. As your traffic exits the Tor network, it could be intercepted or tampered with by malicious actors at that point.
Who Needs It?
As time passes, more people are coming to see the need to keep their location and online activities private.
That said, some groups of individuals are more suited for the amplified protection obtained from Onion over VPN. For these people, the rewards of using the system far overshadow its challenges.
Here are some examples of who might benefit from using Onion over VPN:
- Journalists and whistleblowers: Journalists (especially the investigative kind) and whistleblowers often handle sensitive information and are prone to surveillance or targeting. But combining a VPN and the Tor network makes it extremely difficult to trace anything back to them. This heightened level of privacy allows them to communicate with sources, conduct research, and publish content with increased confidence.
- Human rights activists and dissidents: People who advocate for political or social causes in repressive regimes must communicate and access information securely. What better way to do so than over a system that keeps them anonymous?
- Researchers and people who work with sensitive data: If you’re an academic, researcher, or person working on sensitive topics, Onion over VPN can be helpful. You can maintain confidentiality and anonymity while accessing resources. What’s more, it lets you communicate with colleagues without compromising research objectives.
- Citizens and travelers in restrictive countries: Some governments frown on citizens having free, unlimited Internet access. We’re talking about places like China, Iran, Cuba, Russia, and Vietnam. If you live in a country that blocks access to significant swaths of the Internet, Onion over VPN will help you sidestep those strict censorship or surveillance measures.
- Privacy advocates: At one end of the spectrum, we have people who are unbothered about handing their personal information to corporations. On the other end, people who are branded “privacy nuts” because of the extremes they go to to safeguard their data.
If you consider uber-privacy measures necessary, then Onion over VPN should be high on your selection of solutions. It lets you maintain greater control over your online presence, keeping surveillance, advertisers, data brokers, and other entities at bay.
What About VPN Over Onion?
The idea’s the same: to combine the functionalities of a VPN and the Tor network. However, VPN over Onion follows the opposite routine.
Recall that Onion over VPN routes your traffic through a VPN server before entering the Tor network. On the flip side, VPN over Onion establishes a VPN connection and then routes your traffic through Tor.
This setup provides certain benefits. For one, malicious exit nodes cannot see the content of your data as they would when you use the alternative. In addition, it’s the way to go if you don’t trust your VPN service or don’t want your ISP to see that you’re using one.
But there are several reasons to reconsider using a VPN over Tor.
- It is even slower than Onion over VPN. Expect greater latency and unreliable performance.
- It is complex and challenging to set up. Because it requires manual configuration, it is potentially prone to configuration errors.
- Few providers will work with VPN over Tor.
- You’re limited from accessing websites or services that actively block Tor exit nodes.
- The exit node cannot see your traffic as it would if you used Tor over VPN. However, that leaves it open to the Virtual Private Network’s potential scrutiny. If you use an untrustworthy service, that could be an issue.
And Double VPN?
Double VPN is another way to add an extra layer of encryption over your connection. The feature is also called MultiHop or nested VPN.
This system routes your Internet traffic through multiple servers instead of a single server, as a regular VPN connection would.
Like Tor over VPN, you get upgraded privacy with a trade-off in speed and performance. However, there’s a wider range of options with the former — not all providers offer double VPN as a feature.
If you’re looking to take advantage of such a feature, NordVPN is the place to go.
How to Set Up Onion Over VPN
Here’s how to combine a VPN and Tor for enhanced privacy and anonymity:
- Sign up for a reputable service that supports Onion over VPN (Our recommendation: NordVPN). Your choice should offer robust security features, a no-logs policy, and good performance.
- Download and install the VPN client on your device. You can download it from the provider’s website or official app stores.
- Download and install the Tor browser from the official Tor Project website.
- Launch the VPN app and connect to a server of your choice. We recommend NordVPN’s dedicated Onion Over VPN servers for this case.
- Launch Tor and test the connection by visiting a website that can detect your IP. Confirm that the address displayed is the VPN server’s and not your actual IP address.
Now you start using the Tor + VPN combo to browse the internet.
Best Practices for Onion Over VPN
We’ve discussed its drawbacks, so you know it’s not a perfect system. If you want to mitigate challenges and rest easy, here’s what you need to do:
Go For a Reliable Provider
Virtual Private Networks are cool — but some are cooler than others. That’s why opting for a reputable and trustworthy service is crucial. Each system must work well individually for Onion over VPN to function optimally.
For instance, if your provider is leaky or doesn’t offer vital privacy features like a kill switch, there’s a problem.
To avoid these and other issues, choose a provider with a proven track record, like NordVPN or ExpressVPN.
Read reviews and compare different options to make an informed decision. A reliable VPN provider for the dark web will offer reliable connection stability, robust protocols, fast speeds, and dedicated support to address any concerns.
Perform Software Updates Promptly
To maintain the security and functionality of your setup, ensure your VPN client and Tor browser stay up to date. And just to be safe, do the same for your operating system.
Software updates usually come with critical security patches to address vulnerabilities and protect against emerging threats. If you regularly follow an update prompt, you’re ensuring that your software has the latest security measures in place.
That way, the risks of potential exploits are reduced to near zero.
Keep the Kill Switch On
So you’re using an excellent service, and every app is up to date. But what if you’ve neglected to enable a vital failsafe mechanism that keeps your data from getting exposed?
Every service worth paying for comes with a kill switch. It automatically blocks Internet traffic if the VPN connection drops unexpectedly. This prevents any unencrypted data from being exposed and safeguards your privacy.
Essentially, activating the kill switch maintains a continuous shield of protection even during momentary disruptions. If you use a premium service, these are rare but can happen.
Use Strong Passwords
Strong passwords are a crucial barrier against unauthorized access. They protect your VPN account and associated services from potential breaches, which are more common than you’d think.
For best results, choose complex passwords that combine a mix of uppercase and lowercase letters, numbers, and special characters. Avoid using easily guessable information like birthdays or everyday phrases.
If you’re like most people, keeping track of passwords is a hassle you could do without. Consider using a password manager to generate and securely store your passwords.
Regularly Test Your Setup
Your Onion over VPN setup could work today and be vulnerable tomorrow. Not entirely, of course, but you’re doing this to be as close to perfect anonymity as possible.
Conduct IP address and DNS leak tests to verify that your real IP address remains concealed and your DNS queries are not leaking. Online tools like IPLeak are free and will complete a test in seconds.
Best Onion Over VPN Providers
We’ve selected some of the best VPN services you can use alongside the Tor network.
NordVPN
Some of NordVPN’s 7,400+ servers across 118 countries are special Onion over VPN servers.
As with ExpressVPN or CyberGhost, you’re not limited to the snail-slow Tor browser. So you can use the Tor network on your favorite web browser while staying doubly protected by the VPN. You want to use NordLynx, the provider’s proprietary tunneling protocol built around WireGuard, for best results.
A dark web monitor scans the dark web to keep you informed of any leaks involving you. That’s part of NordVPN’s impressive collection of security and privacy tools. And when you want to switch things up, you can use its Double VPN feature as an alternative to Onion over VPN.
ExpressVPN
ExpressVPN does not offer dedicated Tor over VPN servers, but enables the setup on all its 3000+ servers.
The provider is known for its blazing-fast connection speeds, enabling smooth and uninterrupted browsing, streaming, and downloading. As you can imagine, this comes in handy in mitigating the performance loss the setup causes. We especially like its proprietary Lightway protocol, which goes neck-and-neck with WireGuard for speed.
In terms of privacy and security, ExpressVPN delivers exceptionally. Bank-level encryption, kill switch, obfuscation, and a host of other features will combine with Tor to keep your data safe. Plus, its zero logging policy has been verified, with as many as twelve independent audits over the last year.
CyberGhost
CyberGhost is excellent for this setup, with its capable Onion over VPN connections that seamlessly integrate with the Tor network. It doesn’t have dedicated Onion over VPN servers like NordVPN, but they work for this type of connection either way.
That means you can browse the Tor network on your regular web browser, like Chrome or Firefox. Which is great, as you’re guaranteed significantly better speeds.
On top of that, CyberGhost follows a strict no-logs policy, so it does not store identifiable user data. A vast server network of 12,000+ servers spans 100 countries, offering a wide range of options for securely accessing the internet. In addition, it boasts top-notch encryption protocols to protect your Internet traffic from prying eyes.
Conclusion
Virtual Private Networks and the Tor network are undeniably valuable tools for safeguarding privacy. When combined, they present a system that shields your online data while keeping you as close to anonymous as possible.
If you fall into certain demographics, Onion over VPN can play a big part in keeping who you are and what you do a secret. However, it is overkill if you’re a casual internet user. And if speed is a major consideration for you, you’d be better served sticking to a VPN.
FAQs
⚖️ Is it legal to use the Tor browser?
Yes, it is legal to use the Tor network to browse the dark web. However, there’s a stigma attached to it due to shady activities carried out on the dark web. If you don’t engage in illicit activities, you don’t have to worry. You’ll be on the right side of your country’s laws.
🧅 Is Onion over VPN safe to use?
Yes, it is safe to use for the most part. While there are vulnerabilities in the Tor network’s exit nodes and your traffic can be seen, your identity is protected. It’s either way far safer than using only Tor. That’s why it’s always great to pair it with a reputable VPN service.
🐢 Why is Onion over VPN slow?
That’s because there are several encryption points from when your traffic leaves your device until it reaches the Internet. It passes through the VPN’s tunnel first and then bounces around multiple Tor nodes.